References:
- J. Wang, W. Tang, Q. Zhu, X. Li, H. Rao, and S. Li, “Covert Communication With the Help of Relay and Channel Uncertainty,” IEEE Wireless Communications Letters, vol. 8, no. 1, pp. 317–320, Feb. 2019, doi: 10.1109/LWC.2018.2872058.
- T. V. Sobers, B. A. Bash, S. Guha, D. Towsley, and D. Goeckel, “Covert Communication in the Presence of an Uninformed Jammer,” IEEE Transactions on Wireless Communications, vol. 16, no. 9, pp. 6193–6206, Sep. 2017, doi: 10.1109/TWC.2017.2720736.
- “Best Readings in Covert Communication and Networking | IEEE Communications Society,” IEEE Communications Society, Nov. 04, 2025. https://www.comsoc.org/publications/best-readings/covert-communication-and-networking (accessed Jan. 30, 2026).
- X. Chen et al., “Covert Communications: A Comprehensive Survey,” IEEE Communications Surveys & Tutorials, vol. 25, no. 2, pp. 1173–1198, 2023, doi: 10.1109/COMST.2023.3263921.
- “Limits of Reliable Communication with Low Probability of Detection on AWGN Channels.” Accessed: Jan. 30, 2026. [Online]. Available: https://ieeexplore.ieee.org/document/6584948
What is Covert Communication?
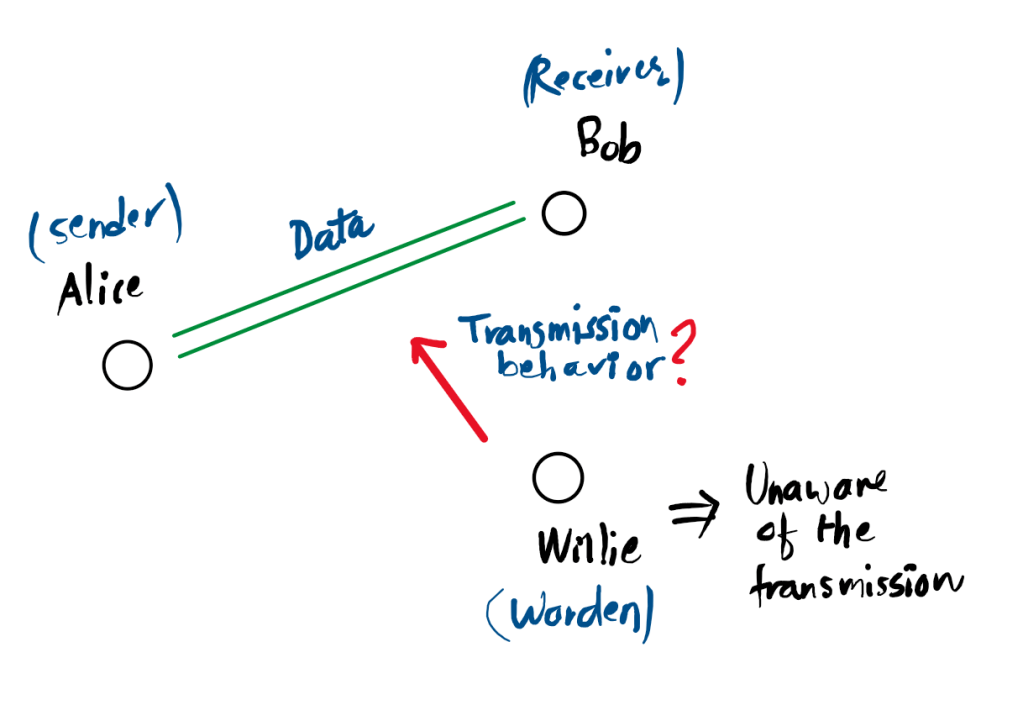
Covert communication, or Low Probability of Detection (LPD) communication, is a security technique designed to hide the very existence of a transmission. Unlike standard encryption, which hides the content of a message, covert communication hides the act of communicating from an observant adversary, often referred to as a “warden” (Willie).
The Fundamental Challenge: The Square Root Law
In traditional additive white Gaussian noise (AWGN) channels, covert communication is limited by the Square Root Law. This law states that to remain undetected by a warden, a sender (Alice) can reliably transmit at most O($\sqrt{n}$) bits of information over $n$ uses of the channel.
If Alice tries to send more than this (i.e., a linear rate of bits), her signal power must be high enough that the warden can statistically distinguish it from the background noise, leading to detection.
Key Components of a Covert System
A basic covert communication model typically involves three parties:
- Alice (Sender): Attempts to send a message to Bob without being noticed.
- Bob (Receiver): The intended recipient who must decode the message despite low signal power.
- Willie (Warden): An adversary who monitors the channel and performs a statistical hypothesis test to decide if Alice is transmitting or if only background noise is present.
One Method: Enhancing Covertness with Jammers
Research has shown that the O(n) limit can be overcome by introducing uncertainty for the warden. One effective method is using a jammer (Jack) who transmits artificial noise.
- Uninformed Jammers: If the warden does not know the exact power level of the jammer, they cannot easily tell if a spike in total power is due to Alice’s signal or simply a fluctuation in the jammer’s output.
- Throughput Gains: This “noise uncertainty” allows Alice to achieve linear scaling (O(n) bits), effectively bypassing the Square Root Law and allowing for significantly higher data rates.
Applications
Covert communication is vital in scenarios where the discovery of a link could lead to negative consequences, such as:
- Military Operations: Hiding tactical signals from enemy surveillance.
- Privacy Protection: Communicating in environments where the mere association between two parties must remain secret.